Pretty Good Privacy (PGP) is one of the most widely used encryption methods used in the world. It was created by Philip Zimmermann in 1991 who believed that the right to privacy is “as apple-pie as the constitution“. GnuPGP, or GPG for short, implements the OpenPGP standard.
Uses of PGP
Encrypt data in transit: while being transferred between two locations (over the local network, internet, etc.) data can be encrypted to prevent a third party from being able to read / open a message
Encrypt data at rest: files sitting on a hard drive can be kept in an encrypted format so that it cannot be opened without providing a correct key
Digital signature: whether it’s a simple text message or a GitHub commit, a PGP signature can help prove “I wrote this”.
How I use PGP
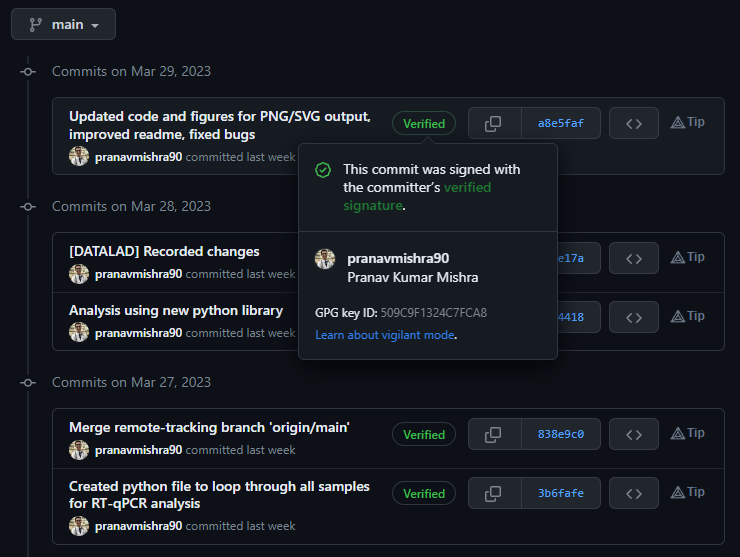
From a practical standpoint, I use PGP encryption and signatures for programming and research purposes. Git is a software used for “version control”. Datalad is a newer software which “wraps” around git and git-annex. I will describe this in a future post. For now, in short, datalad helps you keep track of research data, including what changes have been made to the data set, who made them, and when they were made.
My PGP Public Key
You can quickly add my public key by pasting the following code into your terminal. It will automatically create a new file in your home directory called pranav-mishra-public.key (GPG key ID: 509C9F1324C7FCA8) You can verify that this is the same key I am using to sign commits at GitHub (Tip: you can check the GPG public key of any user by visiting
cat >> ~/pranav-mishra-public.key<<EOF
Pranav Kumar Mishra
Public PGP Key
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQINBGLz/7kBEADGntyMMgvcwH1mM4VImUuBIz3/WpJ6HdvmLZ6G/4dbvuiMPjk4
Q63dAmdTMXC9gYTFchmal7hS9aWWUvY+zkfL+kwuyG2IG1WCJ/XW45QwbPk2kB14
9MH6XD38beQWjWvG2pwudmRNAuS0hBVykq27jVRRd+RVFrkF3Y6UXvVJdaPO4ta/
5JMD6naauOmnWOw2tMzIWlaUnI6hBi4kh75DgMa9VyvT4L3ItJFCppVivZqD0XMb
4COwth2o+wiXcKmskakZZiMw5AEpQ6NTXqOKkWh6uHdEQ0xe/wMpRbTsP0t6aCZO
95KrQqpmh7giyRBdcG070XrpY+u/bLnCCusdRr0XmjJv1vBSdZpVf7T9Mczekfnw
qJnJd0SDjnEmDFkz37D3CDSBRRwDMxJEZbMMWGcmGGqRc5NseOvQdVjeKZFvwZMv
3r0c/fv44pfg9zniygcJmCnwTNwsKxfXPsDfBP/5c+Pkdf0qWila+t4/TaMWemyA
AQxW6sfTag80lcuH++fSzfkXUsBb0RMfuVZg41xxfQyGrBqWuwf2Hk9JJIIwr6Vt
nbyPb1ZlZ3SzOk4fIih9EGfSb86WaHh9laBby5BNXfoRXJMFrRcSxgH+PoEcRG6f
Bs5x482Y4974Zv+gSXHcKiBnwChye5HNJrcLtnNCISx8PIhdty7B1CYxUwARAQAB
tD5QcmFuYXYgS3VtYXIgTWlzaHJhIChQcm90b25NYWlsKSA8cHJhbmF2bWlzaHJh
QHByb3Rvbm1haWwuY29tPokCVAQTAQoAPhYhBDX+miNqyA8/+CmaFVCcnxMkx/yo
BQJi8/+5AhsDBQkB4TOABQsJCAcCBhUKCQgLAgQWAgMBAh4BAheAAAoJEFCcnxMk
x/yodMQQALVVKK7+V9rS07KQRs3kHVPB5+RiS85c8tgHSSalHjQPJy52+qg6I6Ou
BefrvqrBgsR0GqqrugbJTiDWt+ms5bFrUMR/mT1oRXJTOfYbY4Mijj+CtJJEXT5O
8XpNs+xApf+OepUdhZlAUEquwg26Gi9jGAn+K2YegjqRZQ4XXIin9mQ3jEJDVG0h
lDpQiCsfG9fntqhl9XiJaHu9AKR+R/jJNPRnK8AC/qKnIQjnC32AcOuGImHKFLVi
MOHLW/BdcniK4BmyJU5PSUT4lXzSX3mBr0VbnVoCOGaAlo3fPNiN7ua5rhNOV+3d
niwNiri3LZ7EO9wa6LJ6eG6cYTTzkhjIyvcbQ0tpyFvZz/3q/IaCDMqYAjbGl3JB
oFnCxqNfmxQf/W5ZDOY+lhAtuuh57NfBJdS+QdqycERgKLS4tIyQChjwycVnMFmu
NZelCm46FbPpUVw93K/LWjQ+KOZQ7gbsLHdpZhBOKWz5OHIxk2Pb9p3r4Ij6yhQL
bR/lXeOZt9vTh71ZTVJRiyb0yK2pfAESud3jrFyn4mmMu9YUnCbrxHmvRAdtl9Nq
kiPH81VXsPId+FkWE2K/vtWZcr6nWrzy9/GFzolQHhEaJenHGu72j2wItxcEve6I
QouNHWU+q7pYCp5udyDf3dHiawsV1/VJn7e1RctOZHpmSMM+16CWtE9QcmFuYXYg
S3VtYXIgTWlzaHJhIChHaXRIdWIpIDw2MjU2MjcxMitwcmFuYXZtaXNocmE5MEB1
c2Vycy5ub3JlcGx5LmdpdGh1Yi5jb20+iQJUBBMBCgA+FiEENf6aI2rIDz/4KZoV
UJyfEyTH/KgFAmL031gCGwMFCQHhM4AFCwkIBwIGFQoJCAsCBBYCAwECHgECF4AA
CgkQUJyfEyTH/KhD8BAAm5MKDUrdtH+cf4JosD+zF11TQgs2+xCJBq5rwlyemLjj
Q57+lKhEE/jKXKkVJIkR4ClVNzS0KOTTZzY+rMJdkHoPRlz9cNaxTNn4G6g6oaHL
1lDp9qUYYZ5xrdwUTaasW/3d6E1IoCGjcykp+H7b8WwZUmDRdt92UcQ4aX9+zBsY
0SpaL0daOkW2uqVUNTwZvg1SDWLoxlFAg+6Xw3j5KzCpBfndVJyF08LeWHk4MEbs
uxWu7hIG5L9MsRJzgYfgfd6/lpyHWDjq9HVF3OyurDljLWXRCNa/kl3xsajTUnQn
Otgy6VseoD7V+Ygtz8qb0ucaqFSnu9i0DqIE6kkD4OqrKCvMpYf6DkXlh/YRgj2N
Ja3gu48UeZZso00MIf/K9DxBVkqS13RUyHvUtmUCjCLBBVnKkWoWbDrgev8iSQmU
OXGJ6z4t+tGwadz5SzHXDe5ZzQEoVvVL7cDmFbkq8GrlFHXCFUaMghzwErtMToGN
ic2LUmH/UhgggNJUQQxSXSshBwpK94tXR9SQFYMEQYG7YhHW/v6o1xsnm3NfrVmV
AQPodl19s+3IBLA4u/eLiDtYUVmYZCeD8FFlKj1Uts4jL2Q6HOCvpuAEwz7b8ac2
yCeJVaWAqAQyDBRSuQ/EFVfV+tMQSVPSGhv00l/DGTMcP6WTj7iberM9ZY8m/SO5
Ag0EYvP/uQEQALk5XnMSRu5qPCdsW8yi+I5t5k4MjWIqd5fYMboRY4gs1fBuX9tb
lw9dHql/IfQ19Lnr/F8/MQqFyK+phHxqypK30kJ2SD262dl03MWEmUhlwczETCCj
+9h0RNylfDqQsyh8n/Q+UpyrfH5+X96jfh1nAzmm2JqysLNc7dYmqI1IBdJxbSmg
QhzNbM+H113TPdJJXg+5yROWnJo6lq68xp+dm5zdNb8vod9qOWCyC3mujRr9E5t4
3xJf51AowbFPzP2wEm9mY1vb/EgNZDPITngHATd4TI6kQhnvEM7pChRXzSrlbSTs
ZkQpyuPXiPKZzDic/l/O7lkcRvdFs9+Zuh52ZxKwHdskqD6V+iNP89REWQxVCFi0
5l6hk0d9Kqi9oprrgcFRg0kE8pkX7+PNJZRCQDfhfMz8Uy8uFRnm9bdQu3Gs8XD5
a3LTTk4QXGcQauW9l4fFqVHxFZApQn7fn1U9etJMaPaNLBMWTPjQGCVtaVe8c0zS
Fu5GAZ9/YrH2Of8UyksNpKykXaFrm35YUjWXP+hMFysBDoyXwzuGkYt/oCXf7ujw
relcWwwyipZ3zTrSlM3iD4ZUF99ykh7qaGTLVMQ7dHYI9ZGCr8GFrP5Zz5y0k0nI
MgHV0q4ZsuARlYlRZG50+nR0ab+NH9GKwGO9rqtCxxuVJbKjmFYJm7SlABEBAAGJ
AjwEGAEKACYWIQQ1/pojasgPP/gpmhVQnJ8TJMf8qAUCYvP/uQIbDAUJAeEzgAAK
CRBQnJ8TJMf8qGtCEACOtDYC8GgtCxKAfM8rPaASfjni07zLCBSUzjVkv6jMhBq5
/r/AFy71bI/4xzVZgVwjzoYlcLs95yR9qoL2GskBCvNmGwWYLbvCeyfb98GY0vY5
W1LmCsivhOZyMP18A6tbs0g3VMrKgQcWC+oRvrPKcTpD0llrSlqA98jlLtrZ/HNd
/Ym4sbZODjzsYHLxjX9SkL+6c0Jz0EOYLpKcsq+gPg5uGrIQxS/6rw3OoLWflapW
N5hz11CZBpAg8IYzfpY5gM7oENn/ZPnPiNpXu60cYZtpHqNEecwxw+VckZI6w5VF
ZPp5ct4x0CncjXO5luuhFj6kiGkz/FHYOWe1RB3Za3gXCYegF8CttKFKQtYrK2y+
e1uMIYIjqpGJeiypiUvHVvl1p3gb+vhdvl8YWNnQ86UGx9t+NapumtoyNt7ISwxf
iVXeG1tqWD6OUfKLUg1L4staKxuaBQwTGjj0ETMdeOtkAPIip3ZVTMnunsEeM3+o
xg5YyNAPlk+RRz/T/sNOe/vrA/1H1BX05HIx6LoisWTaUsZu6LIENM6nevsMOUoO
NtG+tm/HTWTnP2mkz67K6fAzOOF+MiOHA2mNKxMdxvCtvV5WZiQc4nk1L7t69oPh
5GeZPBErpviXylkWL97g++Zsp89zOE/eI00tMgGZQBCU4pdEhIgZS1M3txrYwg==
=8Owb
-----END PGP PUBLIC KEY BLOCK-----